
WASHINGTON, D.C. – Criminal charges announced this week against multiple alleged hackers in Iran show the breadth of the cyber threat emanating from that country and the FBI and partner agency efforts to neutralize it and hold the individuals accountable.
The hacks included cyber intrusions and fraud, vandalism of U.S. websites, and intellectual property theft from U.S. aerospace and satellite technology companies. In each of the cases, the suspects were believed to be operating at the behest of the Iranian government, or in support of it.
While the cases filed in federal courts in Boston, Alexandria, and Newark are separate and unique, prosecutors and FBI investigators said they send a message that hackers will face consequences regardless of distance and borders.
“No cyber actor should think they can compromise U.S. networks, steal our intellectual property, or hold our critical infrastructure at risk without incurring risk themselves,” said Executive Assistant Director Terry Wade of the FBI’s Criminal, Cyber, Response, and Services Branch. “The FBI will continue to work with our partners to protect U.S. interests and to impose consequences on those cyber actors working on behalf of the Government of Iran in furtherance of their nefarious goals.”
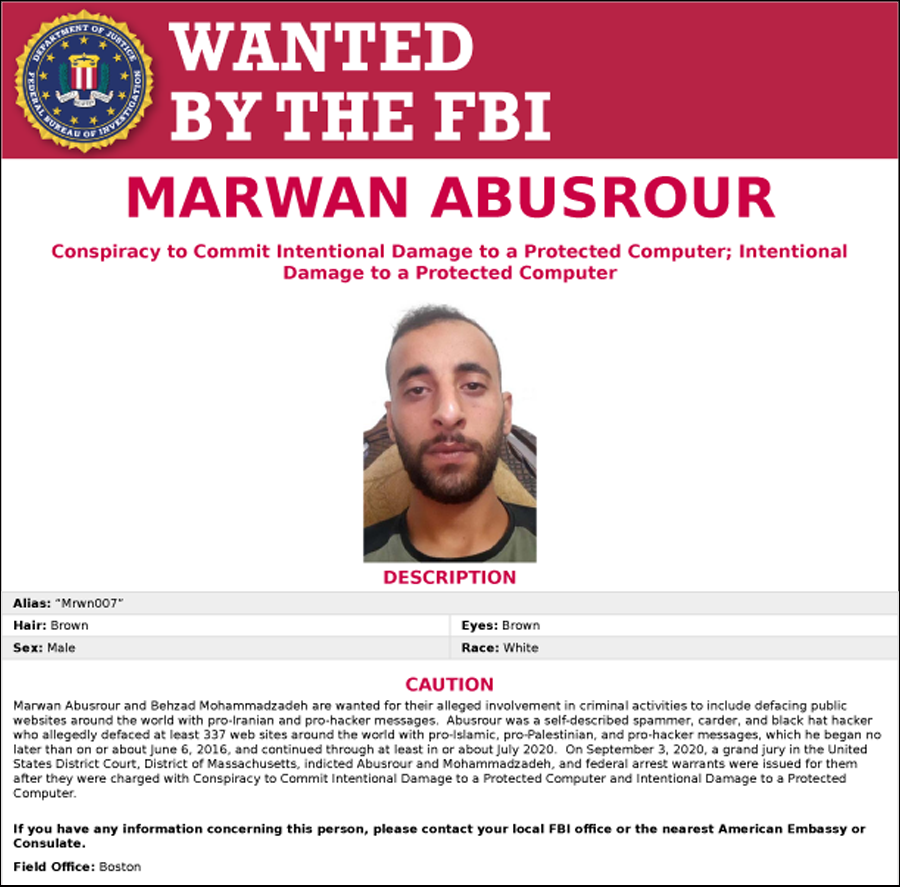
On Tuesday, Behzad Mohammadzadeh, of Iran, and Marwan Abusrour, of the Palestinian territories, were indicted in Massachusetts on charges of damaging multiple websites as retaliation for U.S. military action in January that killed the head of the Islamic Revolutionary Guard Corps-Quds Force, a U.S.-designated foreign terrorist organization.
On Wednesday, Hooman Heidarian and Mehdi Farhadi, both of Iran, were charged in New Jersey in connection with a coordinated cyber intrusion campaign. Investigators allege that the pair, sometimes at the behest of the government of Iran, targeted computers in New Jersey and around the world.

In addition to stealing hundreds of terabytes of sensitive data, the defendants also vandalized websites, often under the pseudonym “Sejeal,” and posted messages that appeared to signal the demise of Iran’s internal opposition, foreign adversaries, and countries identified as rivals, including Israel and Saudi Arabia.
On Thursday, an indictment unsealed in Virginia charged Said Pourkarim Arabi, Mohammad Reza Espargham, and Mohammad Bayati, all living in Iran, with engaging in a coordinated campaign of identity theft and hacking on behalf of Iran’s Islamic Revolutionary Guard Corps, a designated foreign terrorist organization.

According the charges, the defendants’ campaign began back in 2015. At one time, they had a target list of more than 1,800 online accounts, including those of aerospace or satellite technology and international government organizations in Australia, Israel, Singapore, the United States, and the United Kingdom. The three allegedly used social engineering techniques to make contact with those on the target list and assume their identities online. This allowed the defendants to send messages to other unsuspecting individuals that contained malware hidden in links and documents. The malware allowed the hackers access to many additional computer systems.
Also Thursday, the FBI released the details of eight separate and distinct sets of malware used by a front company in Iran to raise awareness of the threat and provide tools to help companies defend their computer networks. The company, Rana Intelligence Computing Company, helped Iran’s Ministry of Intelligence and Security, target at least 15 U.S. companies along with hundreds of individuals and entities from more than 30 countries across Asia, Africa, Europe, and North America. The investigation led to the U.S. Department of the Treasury issuing sanctions against Rana and 45 cyber actors.
The efforts were reflective of the FBI’s new cyber strategy, which is to impose risk and consequences on cyber adversaries—making it harder for both cyber criminals and foreign governments to use malicious cyber activity to achieve their objectives. The new strategy also emphasizes the role the FBI plays as an indispensable partner to federal counterparts, foreign partners, and private-sector partners.
“We want to make sure we’re doing everything we can to help our partners do what they need to do,” said FBI Director Wray. “That means using our role as the lead federal agency with law enforcement and intelligence responsibilities to not only pursue our own actions, but to enable our partners to defend networks, attribute malicious activity, sanction bad behavior, and take the fight to our adversaries overseas.”
Resources:
- Department of Justice and Partner Departments and Agencies Conduct Coordinated Actions to Disrupt and Deter Iranian Malicious Cyber Activities Targeting the United States and the Broader International Community
- Two Alleged Hackers Charged with Defacing Websites Following Killing of Qasem Soleimani
- Two Iranian Nationals Charged in Cyber Theft and Defacement Campaign Against Computer Systems in United States, Europe, and Middle East
- Iranian Hackers Indicted for Stealing Data from Aerospace and Satellite Tracking Companies
- FBI Releases Cybersecurity Advisory on Previously Undisclosed Iranian Malware Used to Monitor Dissidents and Travel and Telecommunications Companies



Comments are closed.